[Turbot On] HIPAA Compliance Controls
Evaluate HIPAA compliance for all your AWS accounts.
Turbot includes thousands of prescriptive cloud controls to ensure cloud environments are secure and cost-optimized. These controls quickly detect issues as they occur and instantly correct misconfigurations. Customers often map Turbot controls to their own Governance Risk Compliance (GRC) tools, and use the resulting evidence to prove continuous adherence to internal controls or external standards such as Center for Internet Security (CIS), NIST 800-53, PCI, GDPR, SOC2, etc.
Over the last year Turbot has open-sourced Steampipe.io, a tool that enables cloud engineers to easily query & report across their cloud, code, logs, and more, using the standard language of data: SQL. Steampipe includes thousands of ready-to-use controls and dashboards that deliver insights into your cloud data. These controls and dashboards leverage a suite of plugins that translate cloud APIs into Postgres tables. One of those plugins, by the way, translates the Turbot v5 API into SQL-queryable tables!
Cloud teams have asked Turbot to also include industry standards within the Turbot platform. We started by open-sourcing thousands of compliance controls, and enlisting the Steampipe community to provide feedback and contributions. Based on community feedback, we are now starting to port these control frameworks into Turbot. Our first addition in Turbot was the Payment Card Industry Data Security Standard (PCI DSS) v3.2.1 standard for AWS, followed by the Health Insurance Portability and Accountability (HIPAA) standard for AWS. Note: When mapping to external standards, Turbot leverages either the published industry standard mapping or the mapping provided by each cloud provider. We are excited to add the HIPAA controls to the platform to complement our existing PCI & CIS Controls, along with AWS, Azure & GCP CIS benchmarks.
This week’s [Turbot On] will look at how to enable HIPAA controls across all your AWS accounts in Turbot.
Traditional Workflow
There are various cloud-native and 3rd-party tools to evaluate cloud infrastructure HIPAA compliance. However cloud-native tools generally work with only one cloud provider, and only do periodic scans. 3rd-party tools may support multiple cloud providers, but fall short on benchmark coverage and, again, scan and report only periodically, missing real-time changes in your environment. These tools often work on a per-account basis, without delivering resource-level granularity. And they are limited in their ability to manage the time-based exceptions that enable you to handle the nuances in your organization.
Get it done with Turbot
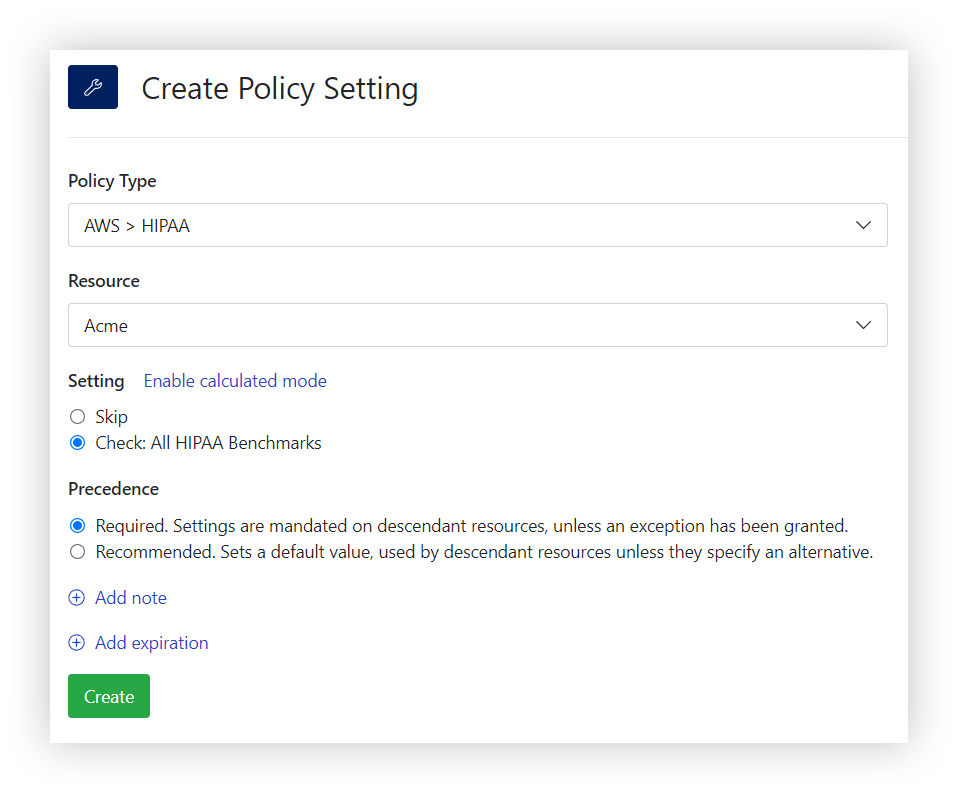
In Turbot, HIPAA guardrails are readily available to control your cloud resource configurations. These guardrails work similar to others, continuously evaluating adherence as changes to your cloud resources occur. First, make sure you have the `@turbot/aws-hipaa` mod installed and any dependent mods installed in your workspace. Then you can enable HIPAA through the following Turbot policy in just a few clicks: `AWS > HIPAA`:
Setting the configuration via the Turbot Terraform Provider is just as simple:
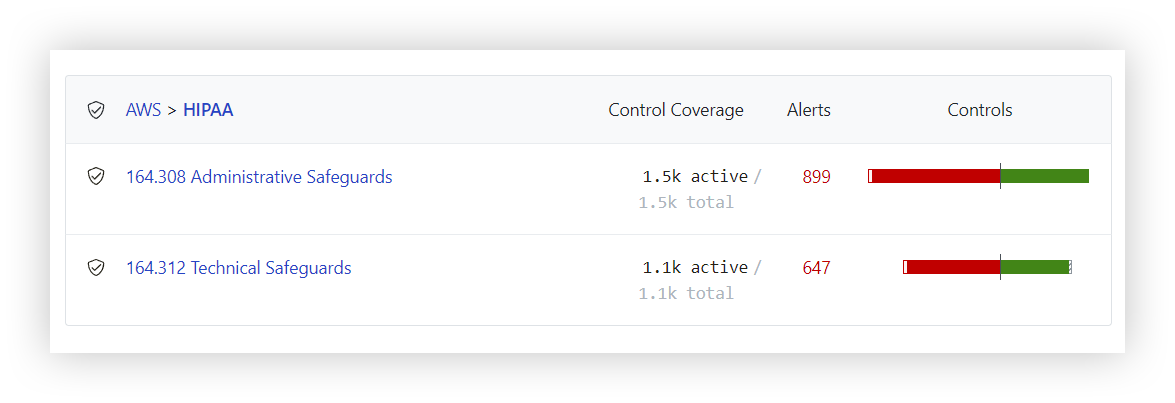
After enabling this policy, Turbot will immediately evaluate all applicable resources compliance with HIPAA. You can view your controls across major sections of the HIPAA standard:
Drill further into subsections:
Drill further to expand the subsections to view particular per cloud service controls:
Analyze which specific resources are impacted per control:
Inverse the view to visualize all primary controls on a particular resource:
Make it happen
See for yourself on how easy it is to view your HIPAA requirements across your cloud resources. If you need any assistance please reach out to Turbot Support, and keep an eye on your inbox for another [Turbot On] post in the near future!
Cheers,
Bob
![[Turbot On]](https://substackcdn.com/image/fetch/$s_!p5XJ!,w_40,h_40,c_fill,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F0bc0c730-9a8a-401c-9db4-d132c3e6d4f5_300x300.png)