[Turbot On] ECR Vulnerability Scanning
Automate vulnerability scanning in all your ECR repositories.
Amazon Elastic Container Registry (Amazon ECR) can be used to host private container image repositories in AWS. This allows teams great flexibility in choice of centralizing or federating repositories for your application teams.
One of the key benefits of moving to a container architecture for your application is to microsegment application functionality with immutable containers for greater security. To maintain that secure configuration, the software libraries used in each container should be scanned for vulnerabilities.
The open source Clair project maintains a list of known vulnerabilities and tools for static analysis of your application containers. Amazon ECR uses the Common Vulnerabilities and Exposures (CVEs) database from the Clair project and provides a list of scan findings. You can review the scan findings for information about the security of the container images that are being deployed.
You can manually scan container images stored in Amazon ECR. Or, alternatively, you can configure your repositories to scan images when you push them to a repository.
In today’s Turbot On we look at how you can easily enable Turbot to enforce automated scanning of every container when they are pushed to your repositories.
Traditional Workflow
The popularity of ECR with application development teams means that you may have dozens (or hundreds) of ECR Repositories across your environment and new ones will be created at any time. Relying on application teams to manually enable scan on push configuration in their development environments can lead to last minute discovery of issues as those teams release software. Automation is needed to support discovery of existing and future ECR repositories, and automated configuration of the scan on push setting.
Get it done with Turbot
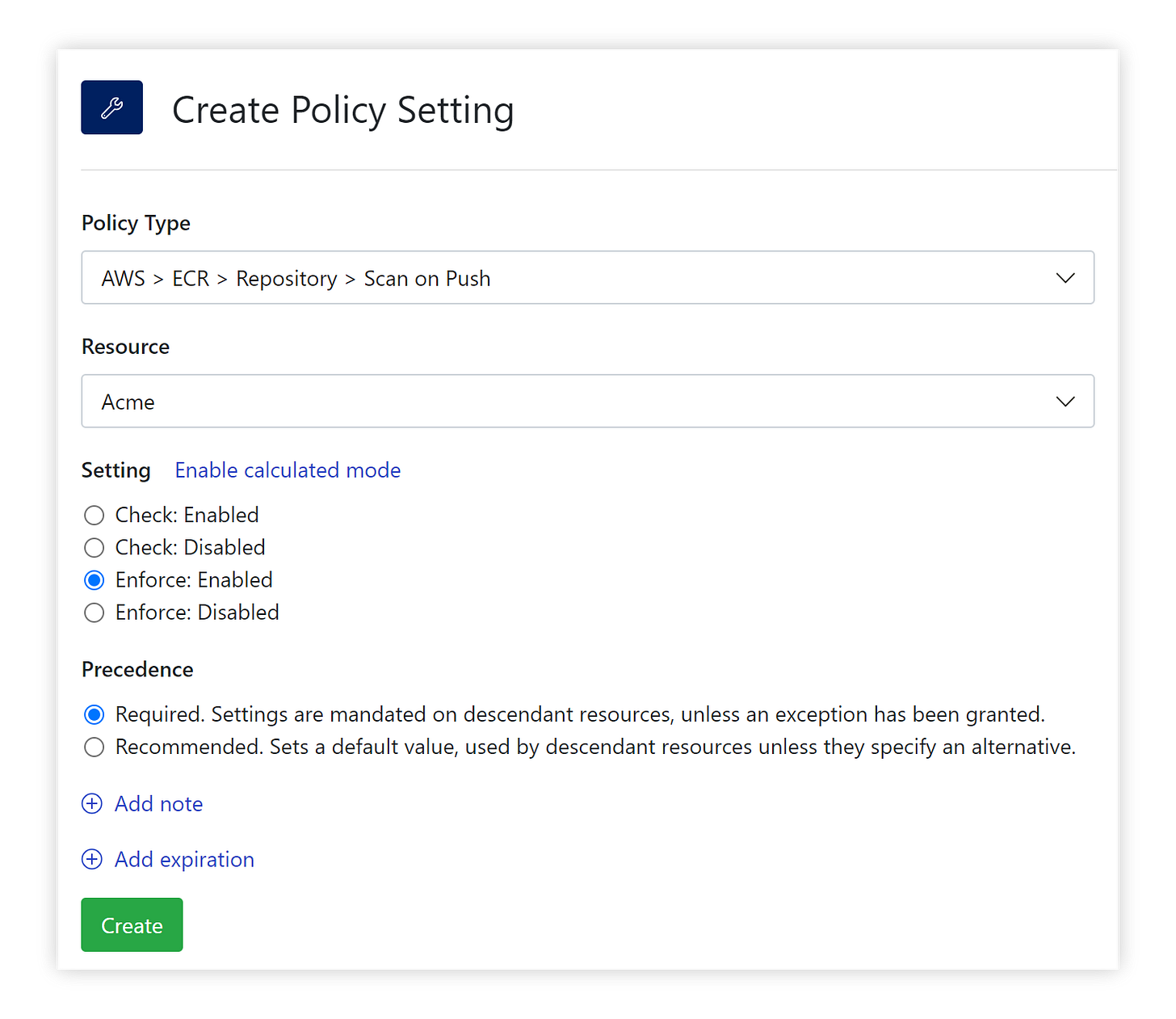
In Turbot, Amazon ECR Repository guardrails are readily available to control your cloud resource configurations. We can set the Turbot automation `AWS > ECR > Repository > Scan on Push` policy in just a few clicks:
Setting the configuration via our Terraform Provider is just as simple:
After setting these policies, Turbot will identify all ECR repositories without Scan on Push enabled and then handle remediation (i.e. enable Scan on Push).
If you are not yet ready to enforce remediation, you can still assess your environment’s ECR Repository Scan on Push compliance by setting the value of the policy to ‘Check: Enabled’ at the Turbot level. In ‘Check’ mode Turbot will alarm on Amazon ECR Repositories that do not have Scan on Push in place. After review of the alarms, selectively apply the enforcement settings or create exceptions as desired.
Given that Scan on Push may not be applicable for all repositories, make use of Turbot’s policy exceptions and time-based expiration settings features to mark exceptions to the rule or automatically reset a configuration when the exception expires.
Make it happen
See for yourself how easy it is to manage your image scanning requirements across your cloud resources. A ready-to-run Terraform template is available to enable this configuration from the Turbot Development Kit (TDK). If you need any assistance please reach out to Turbot Support, and keep an eye on your inbox for another Turbot tip next week!
Cheers,
Bob
![[Turbot On]](https://substackcdn.com/image/fetch/$s_!p5XJ!,w_40,h_40,c_fill,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F0bc0c730-9a8a-401c-9db4-d132c3e6d4f5_300x300.png)