[Turbot On] Automating VPC Flow Logs
Automatically enable AWS VPC Flow Logs for every VPC in under 2 minutes.
AWS VPC Flow Logs enable you to capture information about the IP traffic going to and from network interfaces in your VPC. Enabling Flow Logs are recommended best practice from AWS and the Center for Internet Security (CIS): “AWS CIS 2.09 Ensure VPC flow logging is enabled in all VPCs”; however, it is the customer’s responsibility to enable it in all of their VPCs. This week we will look at how Turbot can help enforce the configurations of VPC Flow logs on every VPC across your organization.
Traditional Workflow
By default VPC Flow Logs are not enabled. If you only have a small handful of VPCs, this is easy to manually enable in an account; however, it becomes a challenge at scale (e.g. many VPCs in a multi-account model) to deploy and keep configurations consistent over time. Typically we see customers who either:
Never enabled Flow Logs and now have the task ahead to configure it across hundreds of VPCs; or
Already have Flow Logs enabled as part of their new account provisioning, but do not have a good way to track and remediate if they are disabled or if new VPCs are created.
Get it done with Turbot
In Turbot, you can use our automated controls to identify which VPCs do not have Flow Logs enabled. In this configuration Turbot’s automation identifies any VPC without Flow Logs enabled as “Not approved”. A separate corrective control has the ability to automate creation of the flow log if it never existed, or re-enable it if someone with elevated privileges disables it.
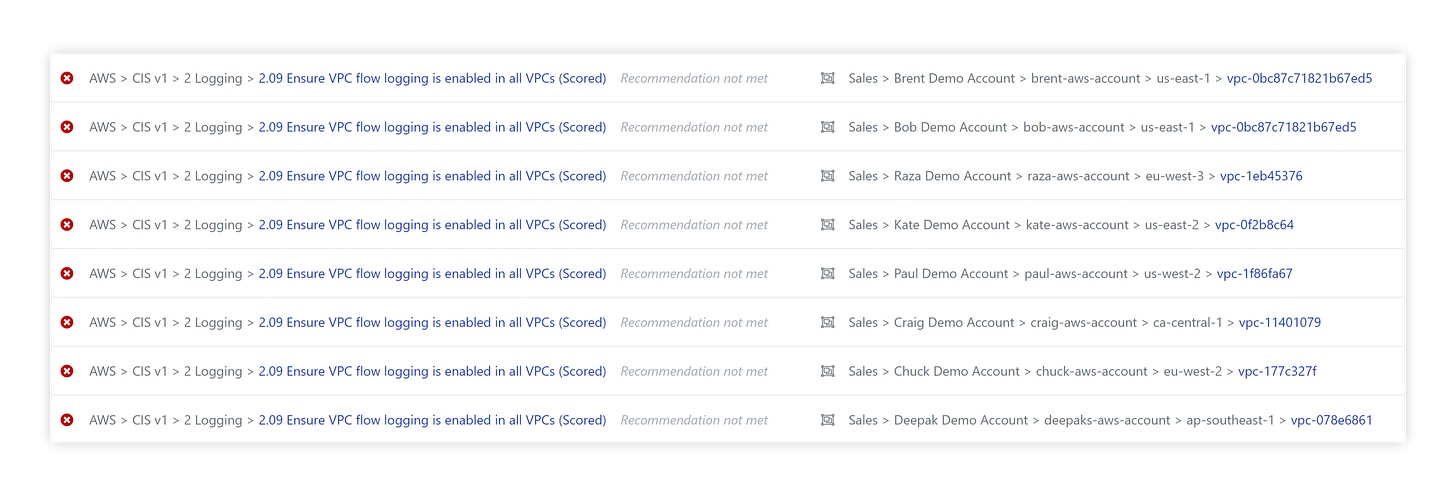
Both Turbot’s own governance controls and our CIS benchmark controls can check for VPCs without enabled flow logging:
CIS Benchmark: `AWS > CIS v1 > 2 Logging > 2.09 Ensure VPC flow logging is enabled in all VPCs`; or
Turbot governance control: `AWS > VPC > VPC > Flow Logging`.
Any alarms that are identified via the detective controls can easily be remediated with just a few policy settings. Once set, flow logs will be continuously managed by the automation to prevent drift.
Create a new policy to enforce automation of your VPC Flow Log Configuration:
In this example we will leverage the default logging configurations to a central S3 log bucket, with both Accept and Reject traffic types. You can tune additional policies for S3 and/or CloudWatch Logs delivery:
S3
Bucket Name: The S3 Bucket that VPC flow logs will be delivered to.
Key Prefix: An S3 key prefix inside the bucket to put the logs.
Traffic Type: The type of traffic to capture in the VPC flow logs. (Accept, Reject or Both)
CloudWatch
Log Group Name: The CloudWatch log group where the VPC flow logs will be delivered.
IAM Role: The IAM role that flow logging will assume to write logs to CloudWatch logs.
Traffic Type: The type of traffic to capture in the VPC flow logs. (Accept, Reject or Both)
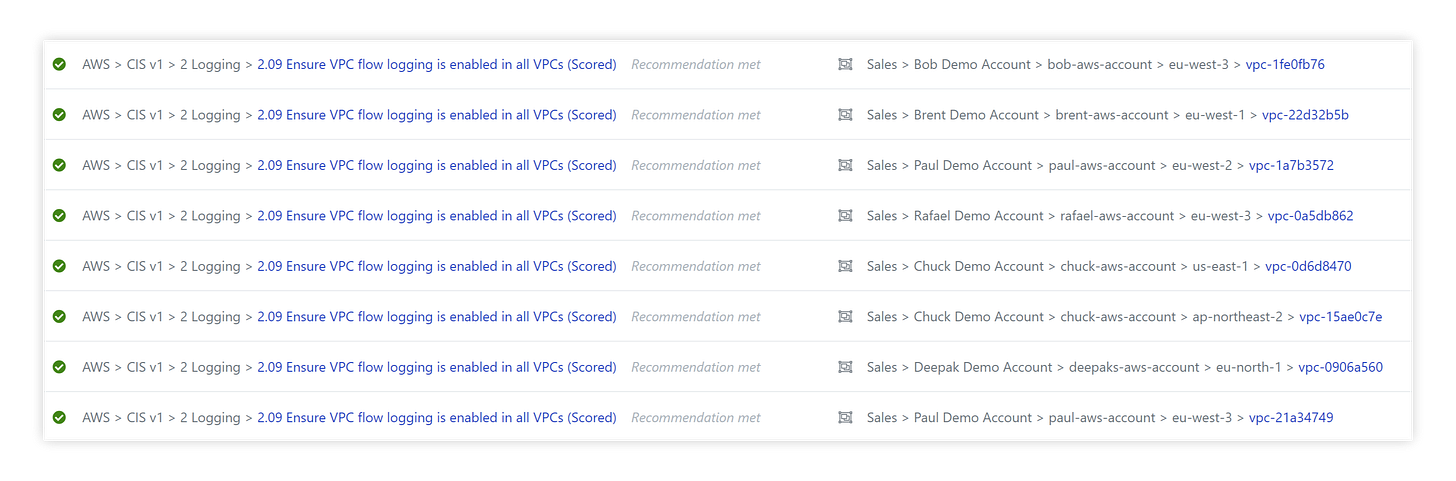
After setting these policies, Turbot automation will correct all the VPCs to enable flow logs, and actively manage these configurations for any new VPCs or changes to existing.
Turbot instantly created the flow logs:
And cleared all the CIS and Turbot alarms:
Make it happen
See for yourself how easy it is to enable VPC Flow Logs across your entire environment with just a few clicks. A Terraform template for enabling flow log checks is available here in the Turbot Development Kit (TDK). If you need any assistance getting this configured in your environment please reach out to Turbot Support, and keep an eye on your inbox for another Turbot tip next week!
Cheers,
Bob
![[Turbot On]](https://substackcdn.com/image/fetch/$s_!p5XJ!,w_40,h_40,c_fill,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F0bc0c730-9a8a-401c-9db4-d132c3e6d4f5_300x300.png)