[Turbot On] Automated Snapshot Cleanup
How to save big by cleaning up older snapshots on a retention schedule.
One of the key benefits of working with IaaS services Amazon EBS, Amazon RDS, etc. is the ability to programmatically create backups and snapshots, but it can also become a source of unchecked cost if not watched closely.
The AWS Backup service, first released in 2019, has the ability to automate backup scheduling and enforce retention policies, but many customers aren’t aware or have existing processes and tools that leave thousands of aged snapshots in their accounts. In addition to our governance controls that enforce AWS Backup plans, Turbot also has additional controls to help manage aging resources (e.g. instance, access keys, storage, volumes, snapshots, etc.) in a consistent, repeatable framework across cloud providers and services.
This week we will look at how to use Turbot’s `Active > Age` policies to delete EC2 snapshots based on your retention policies.
Traditional Workflow
It is very common at scale to see customer environments with backup automation but lacking retention management. While any individual snapshot can be deleted in a few clicks, it becomes difficult to identify snapshots, manage their lifecycle and programmatically remove them across multiple accounts. Often, because of time and personnel changes, it creates compliance risk to delete older snapshots (i.e. "what if someone needs it for something"). Over time, dozens of snapshots turn into hundreds (or thousands) due to this inaction.
Get it done with Turbot
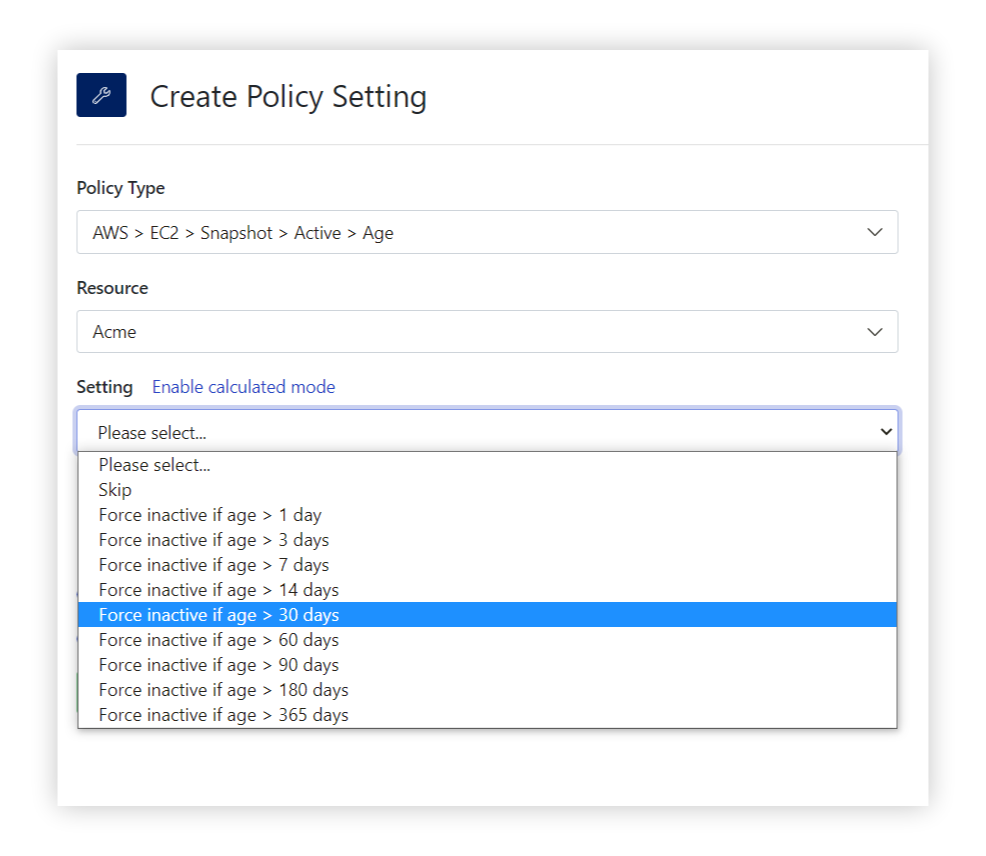
With Turbot, you can use active guardrails to identify if a resource is in active use. Once a resource has been identified as inactive, Turbot has the ability to cleanup the inactive resources with corrective controls, or alert you with detective controls. “Active” type policies have defined sub-policies to calculate the current status based on conditions such as `age`, `last modified`, ‘attached’, etc. One such criteria is the “age” state sub-policy for Amazon EBS snapshots shown in the example below:
After setting the above policies, Turbot’s automation will quickly identify all currently aged snapshots, create an alert and then begin remediation (deletion) once the warning period is over. To evaluate the potential impact of this in your environment (before remediating) we suggest setting the value to `Check: Active` at the Turbot level. You can then selectively apply the enforcement setting to development and/or sandbox environments to test the corrective controls.
Make it happen
See for yourself how easy it is to automate snapshot cleanup in just a few clicks. A ready-to-run Terraform template is available to download to enable these policies from the Turbot Development Kit (TDK). If you need any assistance getting this configured please reach out to Turbot Support, and keep an eye on your inbox for another Turbot tip next week!
Cheers,
Bob
![[Turbot On]](https://substackcdn.com/image/fetch/$s_!p5XJ!,w_40,h_40,c_fill,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F0bc0c730-9a8a-401c-9db4-d132c3e6d4f5_300x300.png)