[Turbot On] Automated EBS Encryption
Automate EBS default encryption for all AWS accounts and regions.
A common headache for cloud operations is dealing with infrastructure that wasn’t optimally deployed from the start. Application teams may not be experts in all areas of infrastructure as code deployment and as such may assume that default settings for their AWS infrastructure implement best practices (like encryption) without the need for them to take an active role in defining all aspects of their infrastructure design.
It is easy for an inexperienced developer or data scientist to use the AWS console to deploy new instances and add storage to them, however the default settings do not enforce many best practices, including encryption at rest for EBS volumes and snapshots.
The good news is that AWS is listening and continually rolling out new options to help address these issues. One such feature is the ability to specify default encryption for EBS resources in each region. This means that any new EBS volumes created in that region will automatically get encryption without any action needed by the developer.
This week’s [Turbot On] will look at how to automate EBS default encryption across all your accounts and regions.
Traditional Model
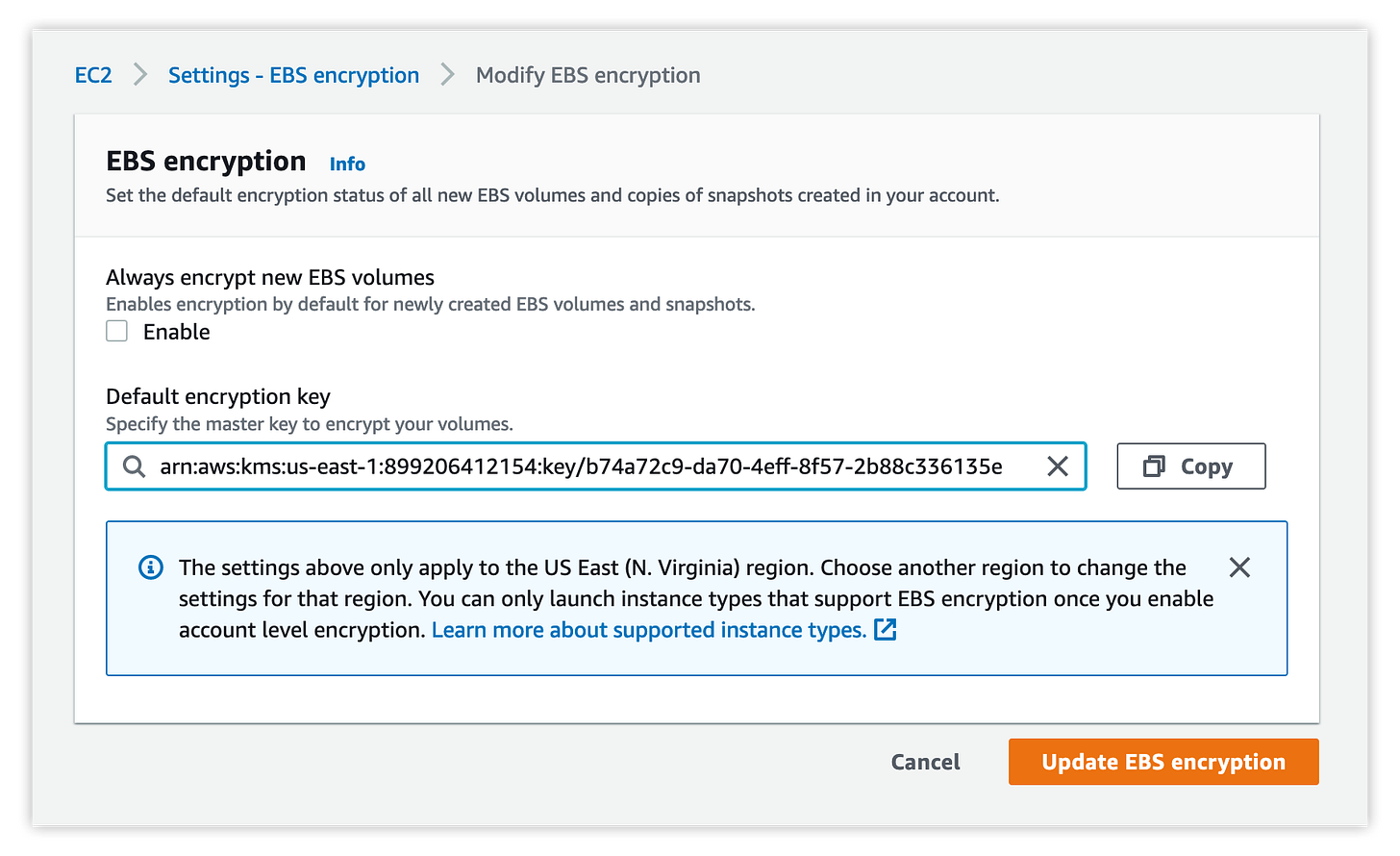
Enabling the default encryption setting must be done for every individual region and account, using this setting in the AWS console:
Performing this action across a couple regions or accounts is trivial, but ensuring that the setting is consistently applied across 20+ regions and hundreds of accounts is 100% a job for automation!
Get it Done with Turbot
Turbot’s automation can ensure that the correct KMS key is setup for EBS default encryption, in every region and across hundreds of accounts simultaneously. Every time a new account is on-boarded, Turbot will identify that the setting is not enabled and set it appropriately without need for any manual intervention.
One policy setting is all it takes:
Setting the configuration via our Terraform Provider is just as simple:
Once this policy is set, Turbot will automatically discover all regions not configured to use default EBS volume encryption and enforce the policy setting. If you are not ready to enforce the change, you can still audit all accounts/regions that do not have the setting enabled, simply change the Turbot policy setting from “Enforce: …” to “Check: …” and Turbot will create alarms for any regions without the correct configuration.
It is important to note that the default setting is just that. It doesn’t apply to already provisioned instances and it can be changed/ignored/bypassed by administrators. If EBS default encryption does not meet your organizations use case, or you want to take a more in-depth preventative approach, you can use Turbot’s EC2 Encryption at Rest controls such as:
‘AWS > EC2 > Instance > Approved > Root Volume Encryption at Rest’
‘AWS > EC2 > Volume > Approved > Encryption at Rest’
‘AWS > EC2 > Snapshot > Approved > Encryption at Rest’
To implement more stringent resource level policy and exceptions around encryption.
Make it happen
See for yourself on how easy it is to manage your encryption at rest requirements across your cloud resources. A ready-to-run Terraform template is available to enable this configuration from the Turbot Development Kit (TDK). If you need any assistance please reach out to Turbot Support, and keep an eye on your inbox for another Turbot tip next week!
Cheers,
Bob
![[Turbot On]](https://substackcdn.com/image/fetch/$s_!p5XJ!,w_40,h_40,c_fill,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F0bc0c730-9a8a-401c-9db4-d132c3e6d4f5_300x300.png)